Xmaze IAST
XmazeIAST Interactivate Application Security Testing Platform
Next-Gen interactive application security testing platform driven by the AI code vaccine tech

Add a small xmirror
Answer your questions
Earlier Security Empowerment
The Xmaze IAST gray box security testing platform is the world's first interactive application security testing platform that utilizes code vaccine technology for transparent crowd-sourced security testing. It seamlessly integrates into existing IT workflows,automates security testing before business code deployment,focuses on addressing over 90% of medium-to-high risk vulnerabilities,and prevents applications from deploying with vulnerabilities,thus ensuring secure operations in the development phase of digital supply chains.
The Evolution of AST
The use of DevOps development model has accelerated the development of projects from monthly to weekly, daily, and even hourly frequencies. However, traditional SAST(static application security testing) and DAST (dynamic application security testing), manual penetration testing, manual code inspection, etc. Cannot keep up with the speed and scale of modern software development and deployment.
Today, IAST (interactive security testing) technology, which is selected as one of the top ten information security technologies by Gartner, combines the advantages of SAST and DAST, while ensuring low false alarm rate and high detection rate. The characteristics of gray box testing enable IAST to be effectively applied to the entire process from development to production, allowing security testing to be seamlessly integrated with SDLC.
| False Positive Rate | Detection Rate | Detection Speed | Third-party Component Vulnerabilities | Language Support | Framework Support | Vulnerability Verification and Exploitation | Risks of Use | Cost | Vulnerability Details | CI/CD Support | |
|---|---|---|---|---|---|---|---|---|---|---|---|
| DAST | Low | Middle | Depending on the URL and Payload Quantity | Depends on Payload and Fingerprint | No Language Distinction | No Framework Distinction | Verifiable Exploitation | Dirty Data, Large Traffic | Lower | Parameters, Request and Response | Low |
| SAST | High | High | With the Amount of Code | Static Scanning Support | Differentiate between Different Languages | Certain Degree of Distinction | Difficult to Verify Exploitation | None | High, Manual Troubleshooting of False Positives | Lines of Code, Execution Flow | High |
| IAST | Very Low | High | Rely on Click Traffic for Real-time Detection | Operational Scan | Differentiate between Different Languages | Certain Degree of Distinction | Verifiable Exploitation | None | Low, Basically no False Alarms | Request Response, Lines of Code, Data Flow | High |
Code Vaccine Endogenous Immunity
All in One


Security Testing
Self-protection
Hotfixes
Comprehensive Vulnerability Detection
As the earliest started, fastest growing, most mature and largest IAST tool in China, Xmaze IAST has unique full-scenario multi-mode vulnerability detection technology that can comprehensively cover vulnerability scenarios and deeply explore security defects and vulnerabilities that are difficult to find with other testing tools from multiple angles; it can judge vulnerabilities based on comprehensive analysis of requests, codes, data flows and control flows, with high accuracy and extremely low false alarm rate; it provides specific positioning information during detection to help developers quickly locate and fix problems, reducing the time and cost of repair.
Multi-source Supply Chain Risk Management in Depth
Xmaze IAST can accurately detect dynamically loaded third-party components and dependencies during the actual operation of the application, identify security vulnerabilities of introduced open source components and open source license risks, and provide reliable suggestions on the difficulty of;
exploiting the vulnerabilities and the compatibility of licenses; supports the import and export of SBOM lists to quickly establish a supply chain asset database;
Connects to XSBOM supply chain security intelligence to realize the process of automated intelligence acquisition-vulnerability detection-vulnerability verification-vulnerability protection.

In-depth Data Security
Xmaze IAST can track the entire life cycle of sensitive data generation-processing-flow-output-storage-destruction between applications, obtain detailed information such as call time, call source, request and response of interfaces containing sensitive information, and associate the results with the API; support flexible definition of sensitive data detection rules, and support classified and graded data security governance, combined with link topology diagrams, to visually display the transmission path of sensitive data and vulnerability risks.

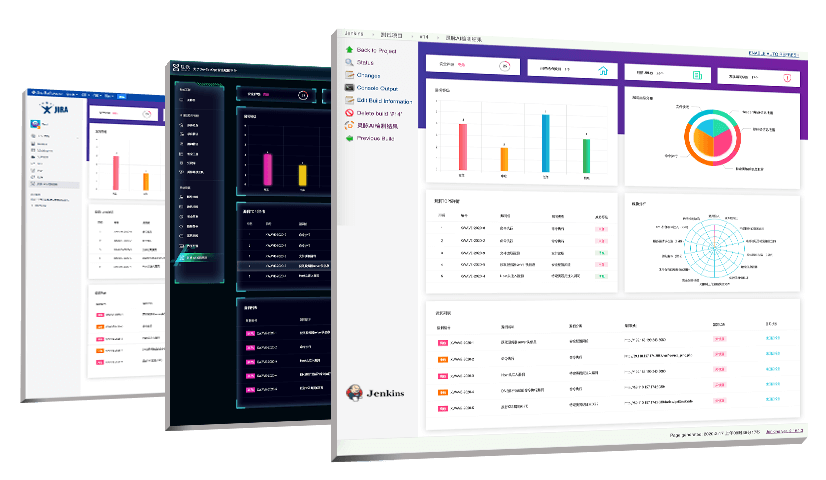

Senseless Process Integration
Xmaze IAST is designed for non-security experts such as R&D, testing, operation and maintenance. Its simple and easy-to-use interface and automated detection capabilities allow anyone to quickly get started and become a security expert. IAST can be integrated into third-party vulnerability management and project management platforms such as Xfuse, Jira、Jenkins. It does not change the original workflow or add additional work content, enabling security novices to obtain security test results while completing functional tests. It helps enterprises improve their security capabilities efficiently and effortlessly, and practice DevSecOps easily.
Clients
The original, patented Fourth-generation DevSecOps digital supply chain security management system, incorporating an "Multimodal SCA+DevSecOps+SBOM risk intelligence early warning ",Innovatively empowers users across various industries such as finance, connected vehicles, telecommunications, energy, government, smart manufacturing, and the broader Internet sector. This system builds a symbiotic and proactive defense framework that adapts to business elasticity, supports agile business delivery, and guides future architectural evolution, continuously safeguarding the security of china's digital supply chain.
Partners
Together with our partners, we are exploring a billion-dollar blue ocean market, jointly driving the implementation of DevSecOps digital supply chain security practices for enterprises, and fostering a symbiotic relationship between business growth and security.
Comments
Awards
-

China Top 50 Technology Companies
-

Forrester
SCA、SAST Evaluated Vendors
-

International Data Corporation
China DevSecOps Innovators
-
Gartner
SCA Evaluated Vendors
-

CDM Group
Next-Gen in Open-Source Security
-

Business Intelligence Group
BIG Innovation Award
-

Internet Security Conference
The Top 10 Innovators of the Year
-

China Academy of Information and Communications Technology
Software Supply Chain Famous Achievement Cases
Certifications
-

National high-tech enterprise
-

CNNVD compatibility certification
-

CAPPVD vulnerability library support unit
-

Intellectual Property Management System Certification
ddd
-

Beijing Intellectual Property Pilot Unit
-

International Quality Management System Certification
ISO9001
-

International Information Technology Service Management System
ISO20000
-

International Information Security Management System
ISO27001
Threat governance from the application source, building a new generation of Digital Supply Chain Security system












 在线咨询
在线咨询